Secure Images
Summary:Using a robust and secure encryption algorithm, we were able to encrypt the image files with just one password, so when its information is tampered with or even manipulated to a high degree, it not only detects it but also recovers it significantly
Full Description:
Today, despite the growing importance of media and information, the word fake news is heard more than ever. The spread of fake news in recent years has been such that the United Nations and the European Union have warned people about the spread of fake news and its dire consequences. Some countries, institutions and organizations have also considered and implemented measures to combat it. Fake news has the potential to jeopardize the security of countries and deprive audiences of free access to accurate information by disrupting the proper flow of information and misleading public opinion.
Meanwhile, photographs are an extraordinary tool for understanding world events. In an age where cameras have become more advanced, cheaper, and more accessible, at the same time, the knowledge of using image editing software and growth in artificial intelligence technology have created the possibility of creation of highly sophisticated fake images. At the same time, this issue has led to the spread of false and misleading information on social media, so that in many cases, the major media could not detect these fake images and used them.
To detect fake images, improvements have been made so far, which has been mainly using neural network algorithms and artificial intelligence, the ability to validate these images can be used only in limited conditions, while not being able to recover the image.
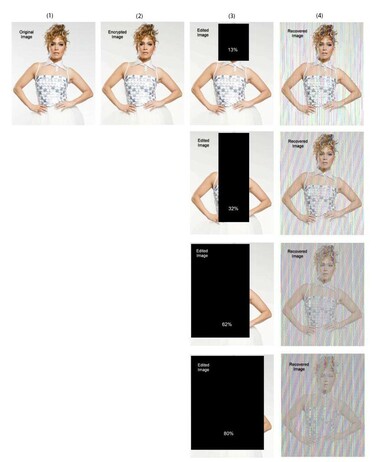
Using a robust and secure encryption algorithm, we were able to encrypt the image files with just one password, so when its information is tampered with or even manipulated to a high degree, it not only detects it but also recovers it significantly. To validate the image files, this software algorithm called Secure Images has been developed to detect the health and retrieve fake image information in Java programming language. The following figure is an example of edited files retrieved by this software. Column one shows the original image and column two shows the image encrypted by this software (Note that file encryption has reduced image quality to a small extent that is difficult to detect with the naked eye). In column three, 13, 32, 62, eighty percent of the information in this image has been edited and completely blackened, respectively. The fourth column shows the output images from this software. It can also be seen however, when 80% of the image is lost, the reconstructed image is recognizable.
Using this technology in cameras or scanners to generate an encrypted output file, in addition to the fact that its password can be a solid document to identify the recipient of the image, gives everyone the ability to control the authenticity of the image.
The coverage area of this very wide technology, for example, includes the following
• All users of social networks
• Spy networks
• Judicial systems and courts where the authenticity and validity of images have a direct impact on their decision
• Society of Journalists
• All government agencies, including immigration agencies, which make decisions based on digital images submitted.
Problem this idea/invention addresses:
This invention addresses the problem we have these days with spread of fake news and fake images with an algorithm able to detect and recover any manipulation in image files. This invention can be used in a variety of industries as we need accurate and original documentations for decision making such as
• All users of social networks
• Spy networks
• Judicial systems and courts where the authenticity and validity of images have a direct impact on their decision
• Society of Journalists
• All government agencies, including immigration agencies, which make decisions based on digital images submitted.
Attached files:
Asking price: [CONTACT SELLER]
Available for consultation? Yes
Invention #12416
Date posted: 2022-01-31
« More Security Inventions
